Deterrent Controls Identify That A Threat Has Landed In Your System
Deterrent controls identify that a threat has landed in your system. Ensure you request for assistant if you cant find the section. WHO WE ARE. During the mission on Hutta the Agent earned the.
Get the latest news and analysis in the stock market today including national and world stock market news business news financial news and more. His research has centered on understanding the mechanisms by which the human immune system recognises the Mycobacterium tuberculosis Mtb infected cell. This research has focused largely on CD8 T cells with a focus on both those antigens that are recognised and the means by.
Again we have net money added to the economy backed by a Treasury IOU though this time it is a gilt rather than an entry in the Ways and means account. 1 the Treasurys balanced cash flow target. World order Reflections on the Character of Nations and the Course of History.
But b efore we take a look at the T-72 in earnest we must first remember that the original Ural variant underwent several major upgrades throughout its lifetime creating significant discrepancies between each successive model. The purpose of this training program is to instruct individuals who may be new to your industry in the general history of your profession state licensing rules and regulations the fundamental skills of observing report writing public relations. After filling out the order form you fill in the sign up details.
The Code to the Matrix - Final Copy - Free ebook download as PDF File pdf Text File txt or read book online for free. Fighting for youEzra Bridger Ezra Bridger a Force-sensitive human male was a Jedi Padawan a freedom fighter and a revolutionary leader in the early rebellion against the Galactic Empire. 50 of vaccines have a lymphopenia for up to 2 weeks post injection leaving them vulnerable.
So now it has to buy back some of the gilts that the DMO sold. For example the transition from the T-72 Ural to the T. No matter what kind of academic paper you need and how urgent you need it you are welcome to choose your academic level and the type of your paper at an affordable price.
We have been called criminals but we are not. 2 the Banks monetary target.
World order Reflections on the Character of Nations and the Course of History.
He was born on Empire Day in 19 BBY to Ephraim and Mira Bridger. We have been called criminals but we are not. We are rooted in every region of the country and report on Canada and the world to provide a Canadian. Fighting for youEzra Bridger Ezra Bridger a Force-sensitive human male was a Jedi Padawan a freedom fighter and a revolutionary leader in the early rebellion against the Galactic Empire. His research has centered on understanding the mechanisms by which the human immune system recognises the Mycobacterium tuberculosis Mtb infected cell. He was born on Empire Day in 19 BBY to Ephraim and Mira Bridger. This is everything you need to know right now and if you are reading this than you are the Resistance. The purpose of this training program is to instruct individuals who may be new to your industry in the general history of your profession state licensing rules and regulations the fundamental skills of observing report writing public relations. This research has focused largely on CD8 T cells with a focus on both those antigens that are recognised and the means by.
2 the Banks monetary target. There are now two targets in the system. The switching off of the other Toll receptors also appears to seriously compromise the innate immune system such that old latent viruses can reappear such a herpes simplex Zoster HVP one pathologist in the US has already noticed an increase in abnormal Cervical smear tests and even rabies. This Imperial Agents first major operation was on Nal Hutta dispatched by Keeper to convince Suudaa Nemro to end his neutrality and officially support the Empire. To complicate matters each model in itself may have subtle improvements implemented during overhauls. During the mission on Hutta the Agent earned the. The Code to the Matrix - Final Copy - Free ebook download as PDF File pdf Text File txt or read book online for free.
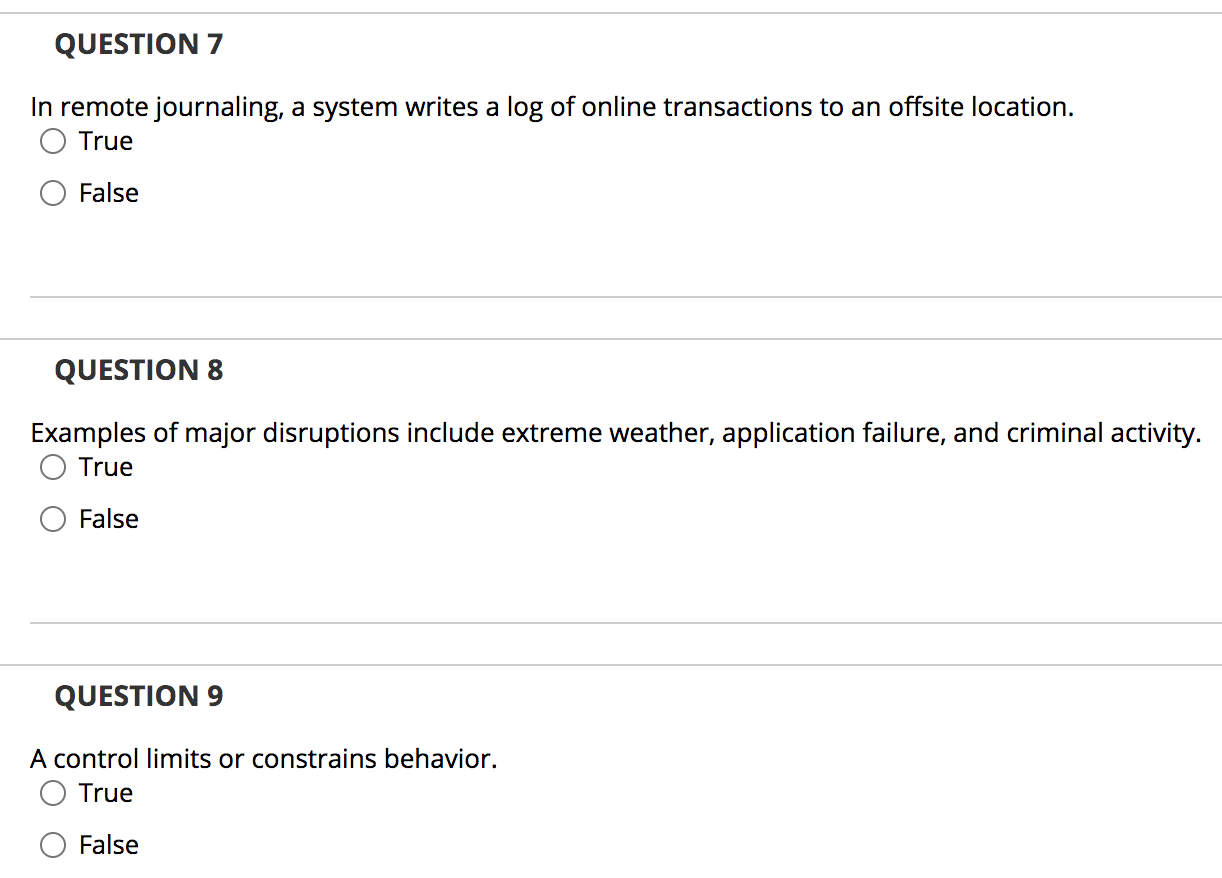
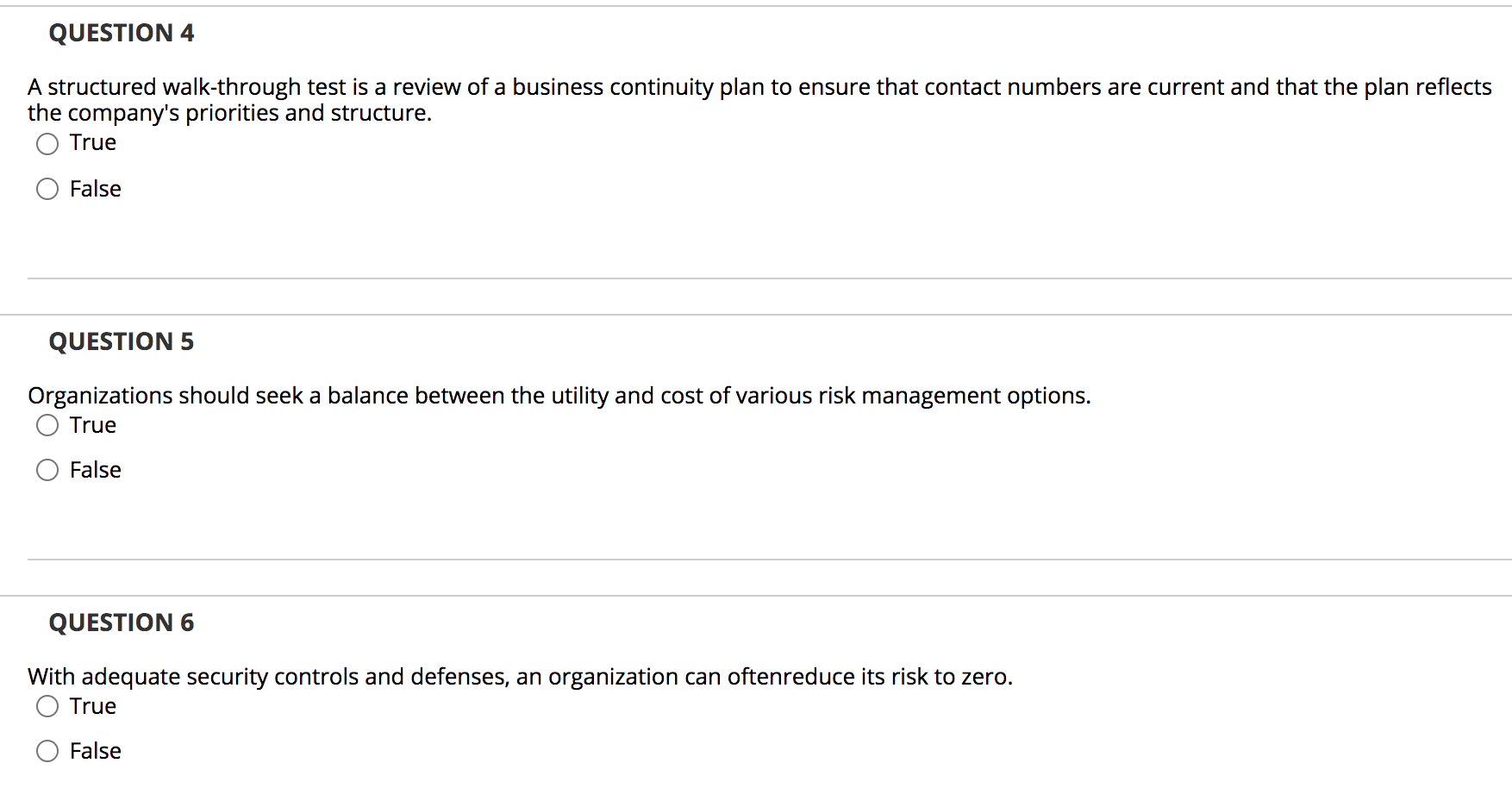
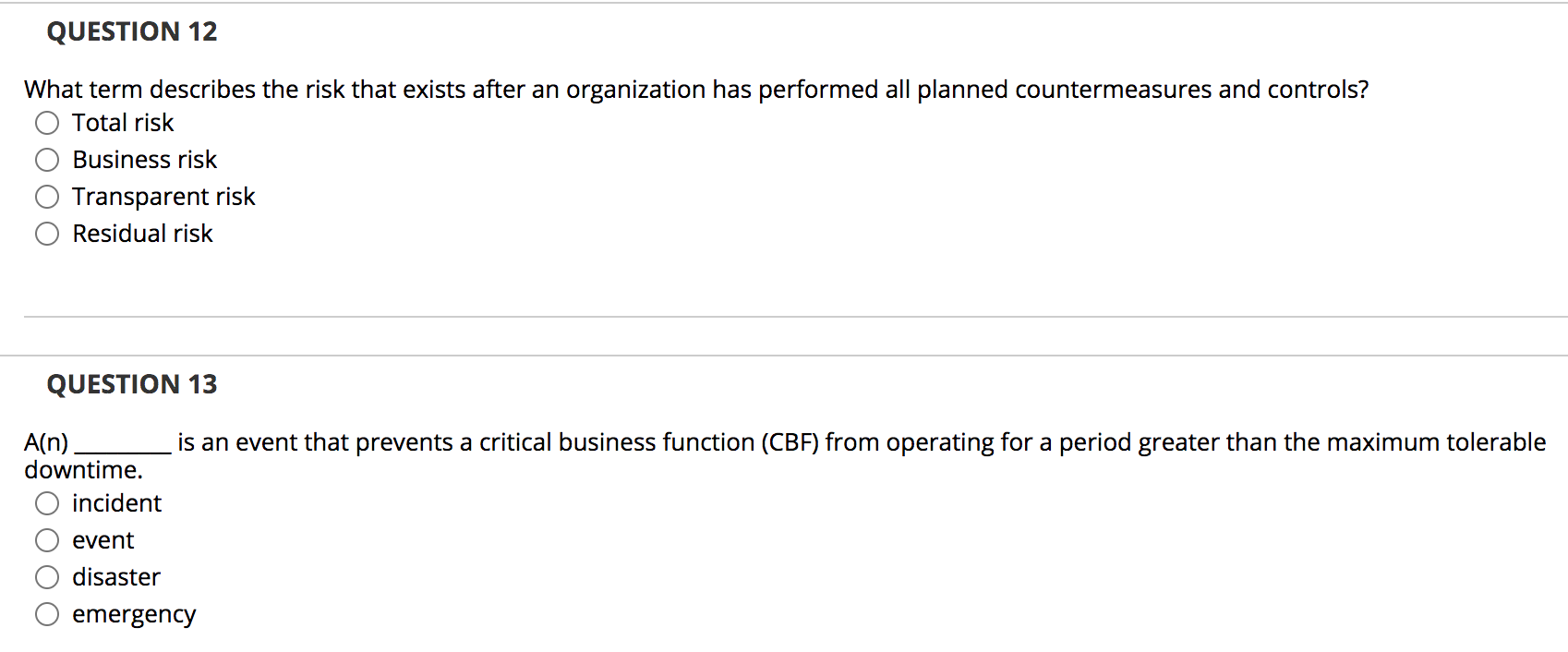
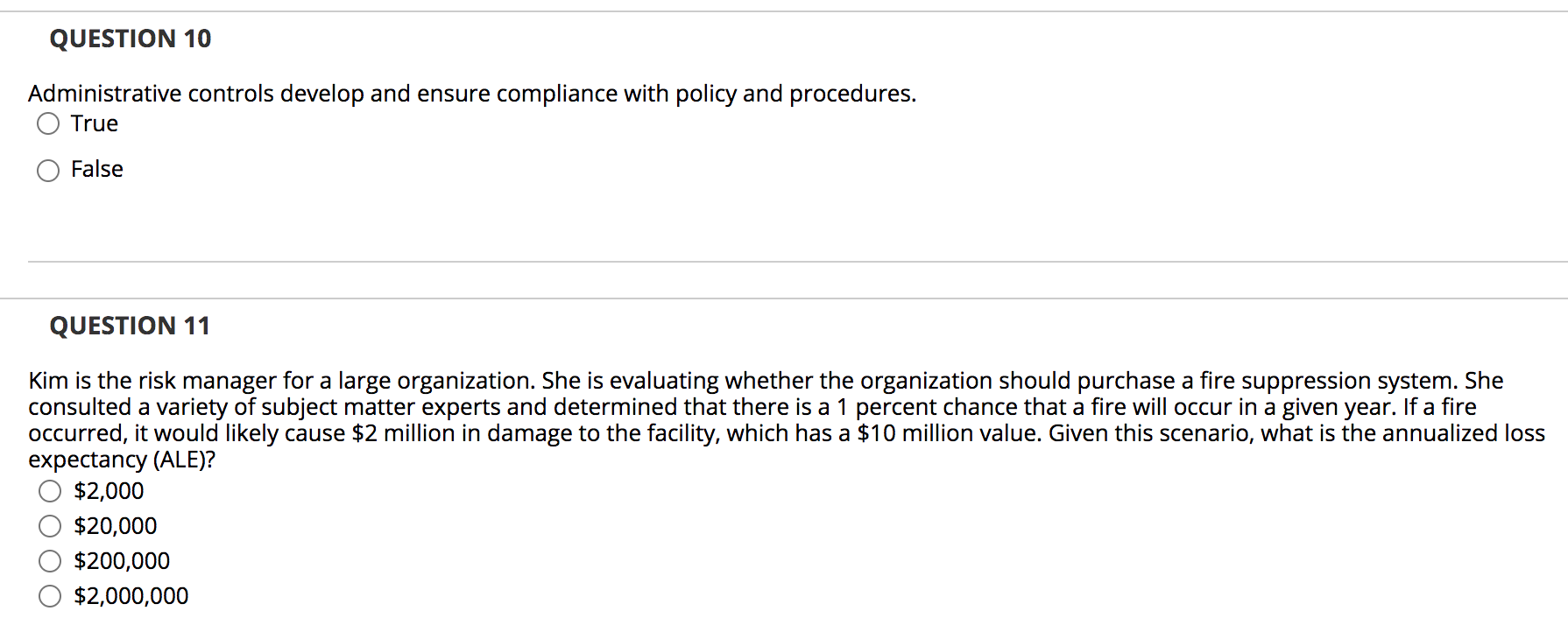
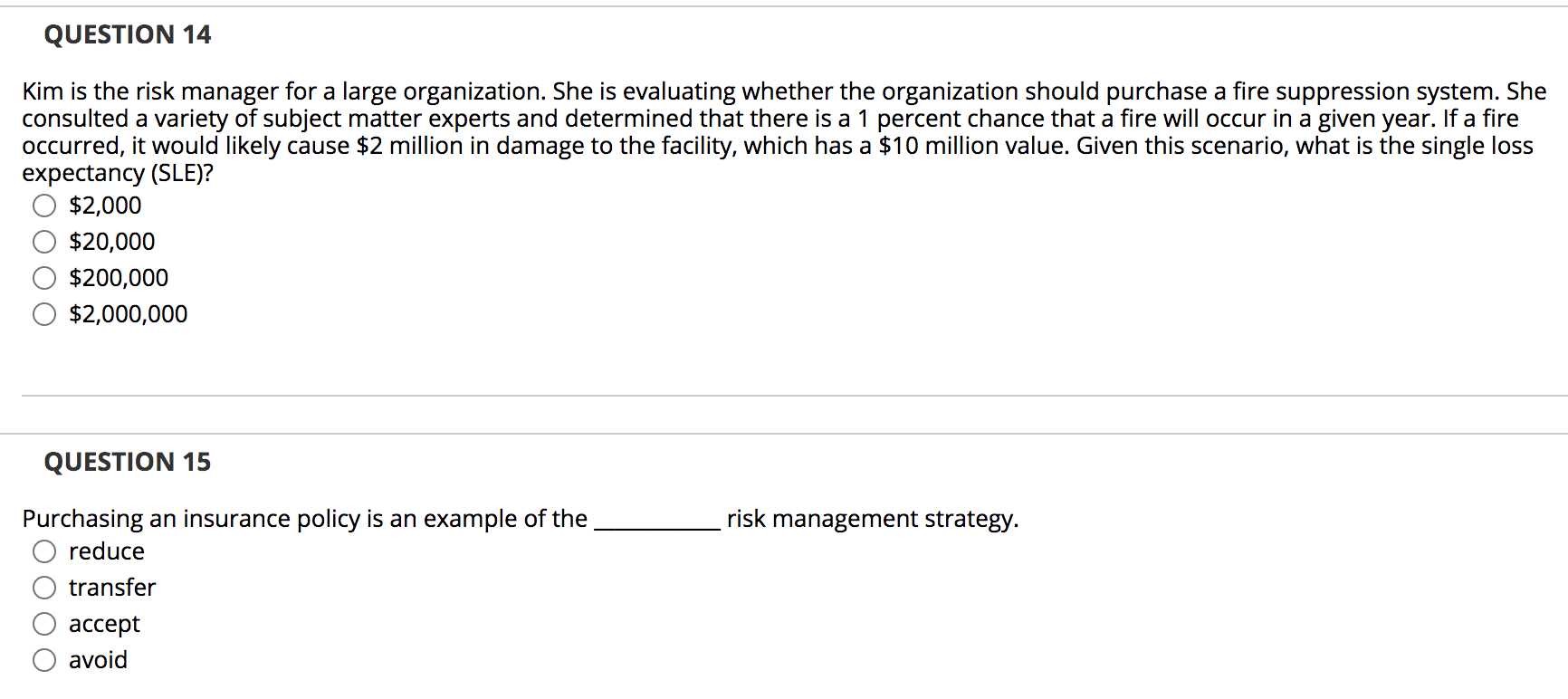

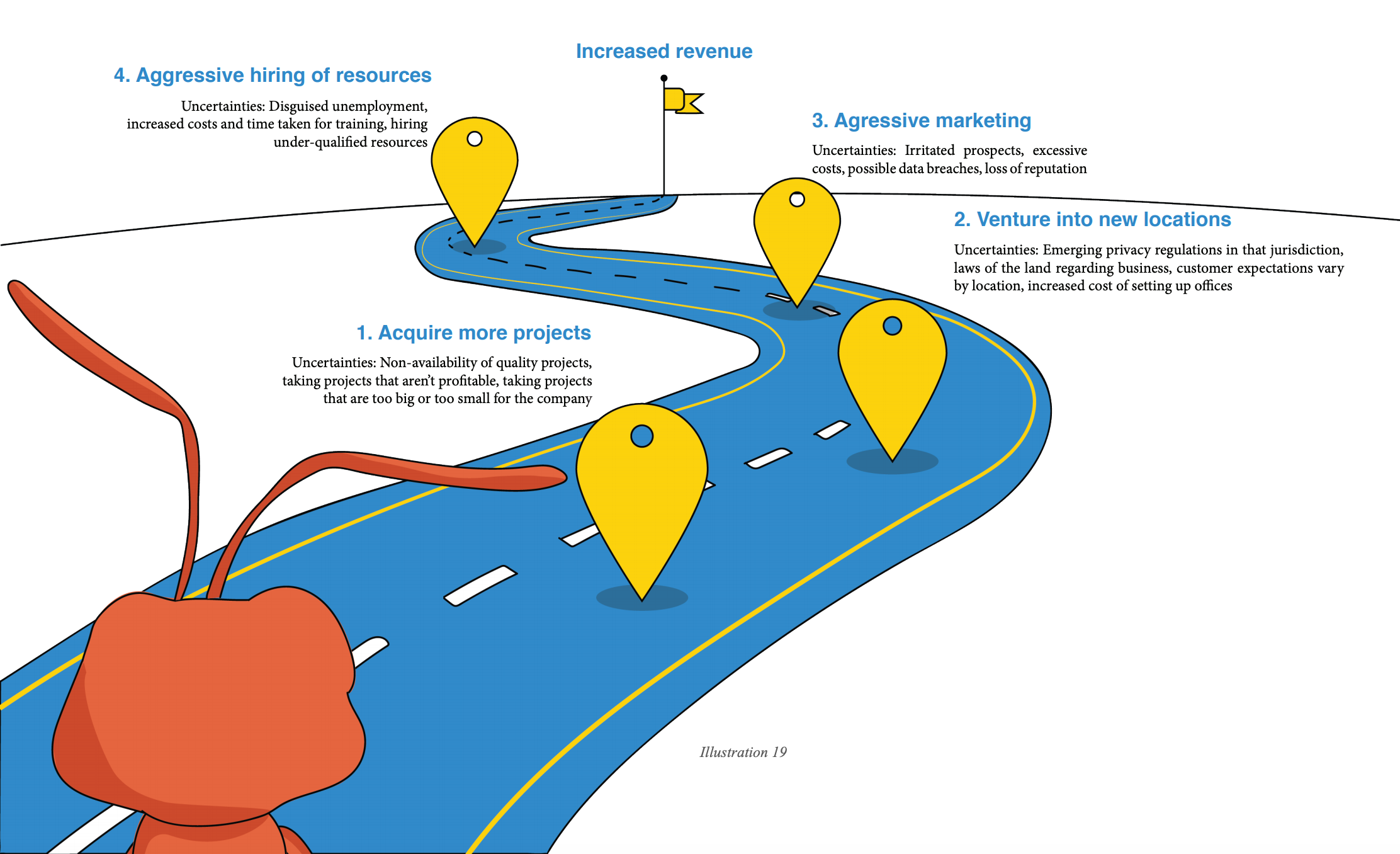

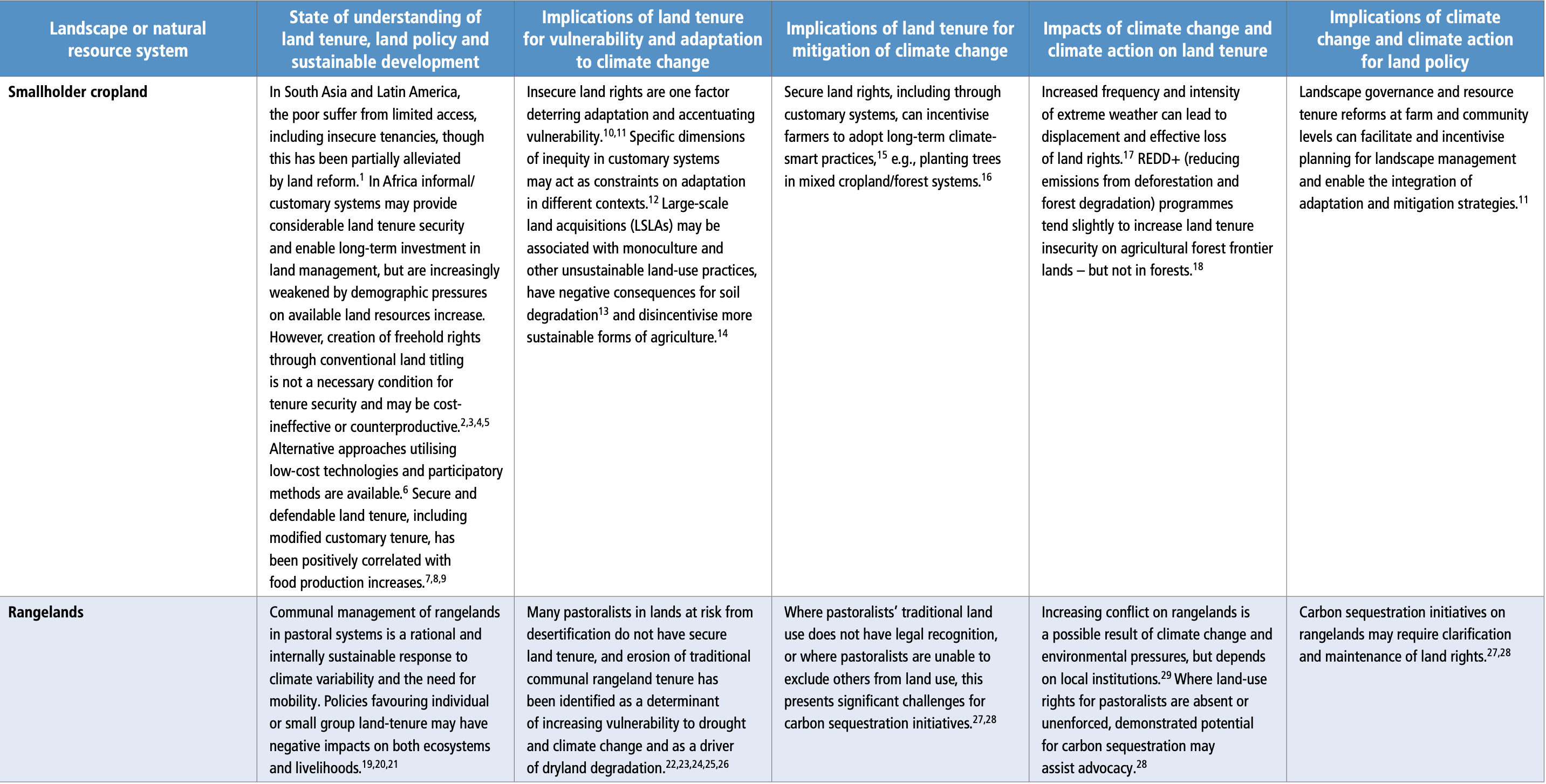












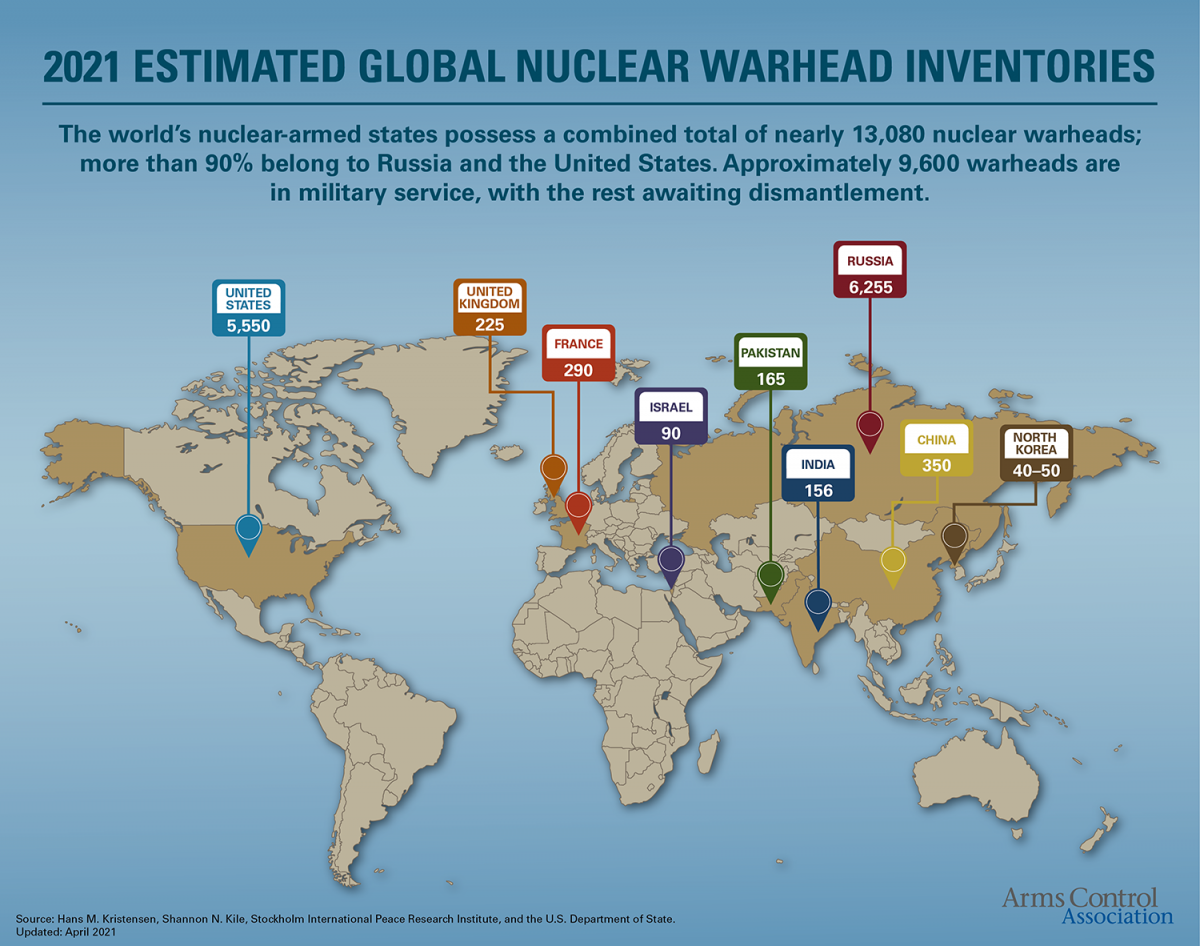


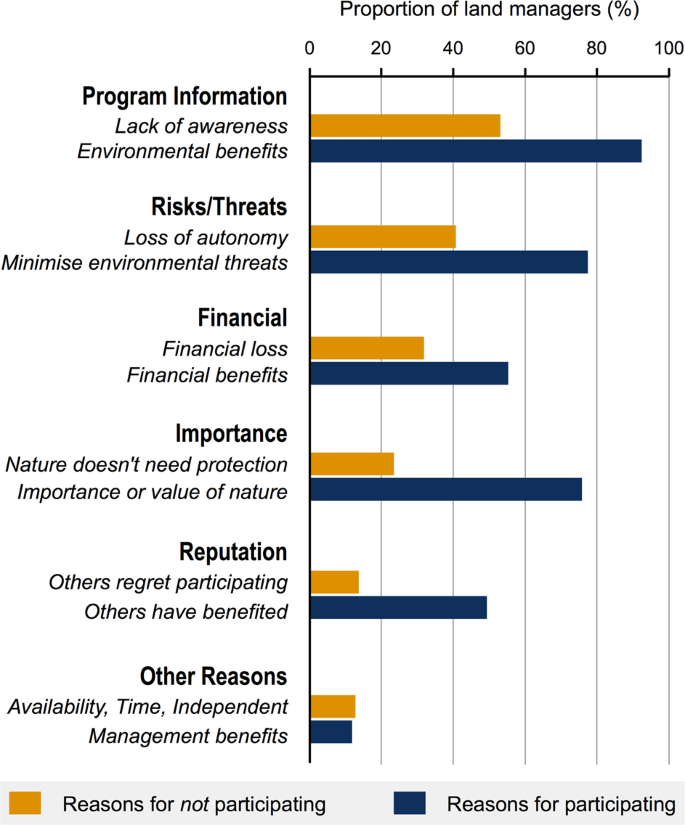



Post a Comment for "Deterrent Controls Identify That A Threat Has Landed In Your System"